In today’s digital age, where personal identification plays a pivotal role in our everyday transactions and interactions, the importance of securely storing biometric data cannot be overstated.
This guide aims to shed light on the complex mechanisms behind biometric data storage, examining the technologies employed, the robust security measures in place, and the ever-evolving landscape of privacy issues and regulatory frameworks.
As biometric authentication becomes increasingly commonplace, from unlocking smartphones to securing bank accounts, a deeper understanding of how your biometric data is stored is essential for anyone looking to protect their digital identity.
Biometric data captures the unique physiological and behavioural traits of individuals, offering a reliable method for digital identification and authentication. This category encompasses a diverse range of characteristics, such as fingerprints, facial patterns, iris configurations, and voice wavelengths.
These attributes are not only unique to every individual but also difficult to replicate or forge, making them highly valuable for secure identification purposes.
The allure of biometric data lies in its robust security and unmatched convenience. Unlike traditional security mechanisms, which may include passwords or physical tokens that can be forgotten, lost, or stolen, biometric data offers a secure and user-friendly alternative. It streamlines authentication processes across numerous applications, enhancing user experience while bolstering security measures.
This dual benefit has propelled its adoption across various sectors, including finance, healthcare, and personal device security.
Biometric identification systems leverage a range of physiological and behavioural characteristics, with fingerprints, facial recognition, iris scans, voice recognition, and vein patterns being among the most prevalent.
Emerging technologies are expanding the scope of biometric data types further. Gait recognition, for example, identifies individuals based on their walking patterns and body movements. This method provides a non-intrusive way of recognising individuals, even at a distance.
The collection of biometric data integrates advanced technologies to ensure accurate and reliable identification.
The storage of biometric data relies heavily on advanced encryption algorithms and secure storage solutions. Data encryption plays a pivotal role, converting biometric information into a scrambled format that can only be decoded with the correct decryption key. This approach significantly mitigates the risk of data breaches, ensuring that biometric data remains confidential and intact.
Secure databases and storage systems further protect this data, employing multiple layers of security to guard against unauthorised access and tampering.
The debate between on-device and cloud storage of biometric data centres on the balance between security, privacy, and accessibility. On-device storage ensures that biometric data remains localised on the user’s device, offering a high degree of privacy and reducing the risk of mass data breaches. This method is particularly prevalent in smartphones and personal electronic devices.
In contrast, cloud storage involves storing biometric data on remote servers, enabling seamless access across multiple platforms and devices. While this increases convenience and flexibility, it also introduces potential vulnerabilities, as data stored in the cloud may be susceptible to hacking and unauthorised access.
The choice between on-device and cloud storage depends on the specific requirements and risk assessments of the application in question.
Encryption is the cornerstone of biometric data security, transforming raw biometric information into a coded format that is virtually impossible to decipher without the correct decryption key. This process employs sophisticated algorithms to scramble the data, ensuring that even if unauthorised parties access the information, they cannot interpret or misuse it.
The strength of the encryption is critical, with advanced encryption standards (AES) commonly used to provide robust protection for biometric data.
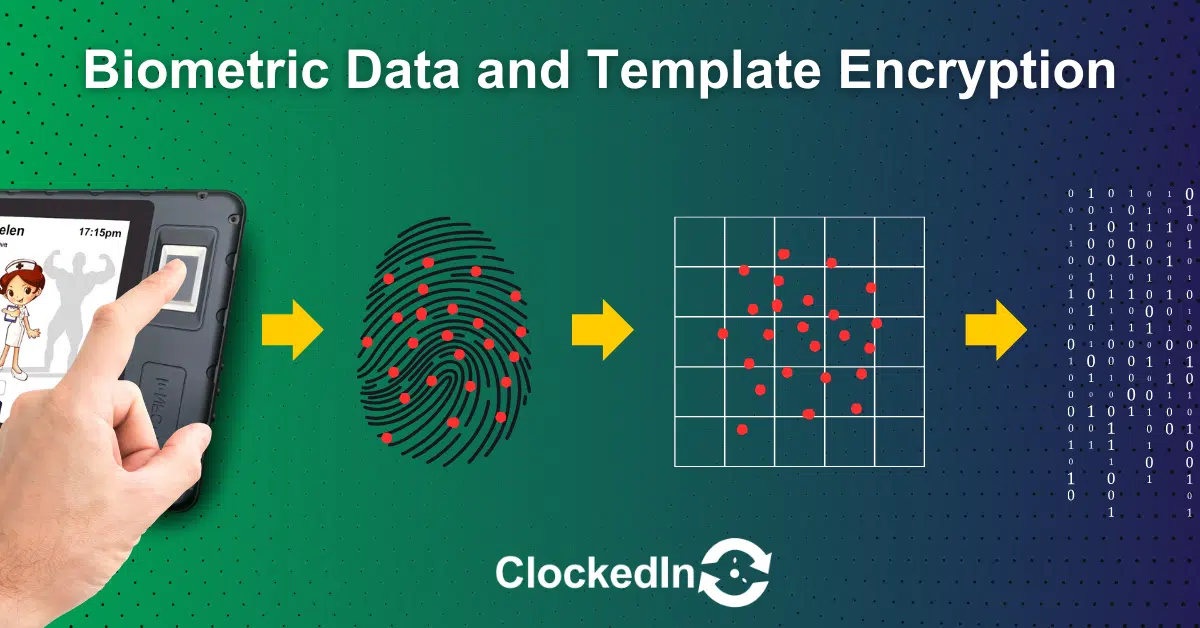
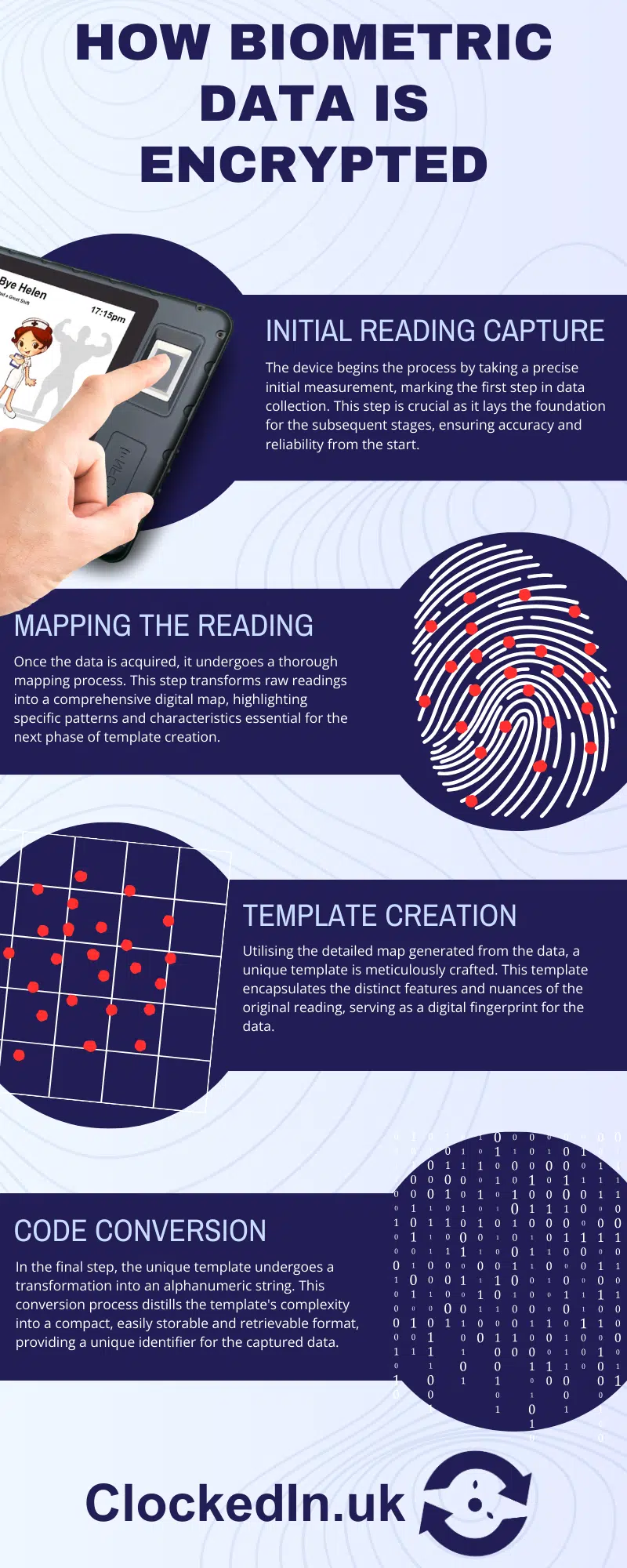
Template storage represents a strategic approach to storing biometric data, focusing on efficiency and security. Instead of storing raw biometric images or recordings, the system extracts and stores a digital representation – a template – that encapsulates the essential features of the biometric data. This template is significantly smaller in size and does not contain the full image or recording, reducing storage requirements and enhancing security.
The template storage process involves analysing the biometric sample, identifying distinguishing features, and encoding these features into a compact, encrypted template. This method ensures that the stored data retains its unique identification capabilities while minimising privacy risks and storage demands.
To safeguard biometric data, a comprehensive array of security protocols is employed, spanning encryption, secure storage, access controls, and regular security audits. Encryption, as previously discussed, plays a vital role in obscuring the data, making it indecipherable to unauthorised entities.
Against the backdrop of evolving cyber threats, maintaining the security of biometric data requires a dynamic and multifaceted strategy. This includes the implementation of advanced cybersecurity technologies, such as end-to-end encryption for data in transit and at rest, two-factor authentication for system access, and blockchain technology for decentralised data storage with enhanced security and traceability.
Furthermore, continuous monitoring and real-time threat detection systems play a crucial role in identifying and responding to potential security breaches swiftly, thereby ensuring the ongoing protection of biometric data.
Biometric data is inherently personal and, if compromised, can lead to severe privacy violations and identity theft. Unlike passwords or PINs, biometric characteristics cannot be changed, making the stakes of securing this data exceptionally high. The risks include unauthorised tracking and surveillance, potential misuse of data for discriminatory purposes, and the risk of permanent identity theft if the data is compromised.
Globally, various laws and regulations have been enacted to protect biometric data, including the General Data Protection Regulation (GDPR) in the European Union, which sets stringent requirements for the processing of biometric data.
In the United States, the Biometric Information Privacy Act (BIPA) in Illinois is among the most comprehensive laws, requiring informed consent for the collection and storage of biometric data and establishing standards for its protection.
Other regions may have less stringent or more sector-specific regulations, reflecting the growing recognition of the need to protect this sensitive information.
One of the primary technical challenges in storing biometric data is ensuring its security against increasingly sophisticated cyber threats. As biometric data is irreplaceable and highly personal, any breach can have severe consequences. Scalability presents another significant challenge, as systems must manage vast amounts of data efficiently without compromising performance or security.
Additionally, ensuring the accuracy and consistency of biometric identification across diverse populations and conditions (such as aging, injuries, or changes in voice) requires advanced technologies and ongoing system updates.
ClockedIn employs AES-256 encryption for the storage of its biometric data, adhering to a security standard that is both highly secure and robust. This encryption method involves transforming the biometric templates—digital representations of an individual’s unique biometric identifiers—into encrypted code. The AES-256 standard, notable for its 256-bit key size, is recognised for its exceptional security level, currently deemed unbreakable with conventional computational means. This ensures the encrypted biometric data remains securely protected and inaccessible without the appropriate cypher or decryption key.
It’s important to note that AES-256 is the same encryption standard used by the U.S. government and military for securing classified and sensitive information. Its adoption by such high-security organisations underscores the standard’s reliability and effectiveness in protecting data against potential cyber threats and unauthorised access.
By utilising AES-256 encryption, ClockedIn not only ensures that the stored biometric data is safeguarded but also aligns with the security protocols trusted by the U.S. government and military. This approach highlights ClockedIn’s commitment to the highest data security and privacy standards, reinforcing user trust by demonstrating that their personal biometric information is managed with the highest care and security measures available.
The collection and storage of biometric data raise several ethical concerns, including issues of privacy, consent, and potential misuse. There’s a risk of surveillance and loss of anonymity, especially if biometric data is used without explicit consent or for purposes beyond its original intent. Additionally, the accuracy and bias in biometric systems can lead to discrimination and unequal treatment of certain groups, highlighting the need for ethical guidelines and oversight.
Mitigating these ethical concerns requires a multi-faceted approach. Transparent policies and practices regarding the collection, use, and storage of biometric data are crucial. This includes obtaining informed consent from individuals and providing them with control over their data. Implementing rigorous standards for accuracy and fairness in biometric systems can help reduce bias and ensure equitable treatment. Moreover, regulatory frameworks and ethical guidelines should be established and enforced to guide the responsible use of biometric technologies.
The journey through the landscape of biometric data storage reveals a technology that is both powerful and challenging. As we move forward, the potential of biometric storage to enhance security and user experience is clear, yet it is accompanied by significant responsibilities. The future promises advancements that will continue to transform this field, but it is essential that these developments are guided by ethical considerations and a commitment to protecting individual rights and privacy.
Embracing the opportunities while navigating the challenges will be key to unlocking the full potential of biometric data storage, ensuring it serves as a force for good in the secure identification and authentication of individuals across the globe.
Biometric data storage employs advanced encryption and security measures, making it highly secure. However, like all technologies, it is essential to implement and maintain robust security protocols to protect against evolving cyber threats.
While biometric systems are designed to be secure, no system is entirely immune to hacking. Continuous advancements in security technologies are necessary to mitigate these risks.
Biometric data is increasingly used for authentication in smartphones, banking, healthcare, and security systems, offering a convenient and secure alternative to traditional passwords.
The primary benefits include enhanced security, increased efficiency in authentication processes, and improved user experience.
Challenges include ensuring the security and privacy of stored data, addressing potential biases in biometric systems, and managing the scalability of data storage solutions.

Address: Suite 6 Empingham House, Uppingham Gate, Uppingham, LE15 9NY
Tel: 0203 371 1006
Specialising in time and attendance software, we deliver tailored solutions that streamline workforce management and boost productivity.
Cube Purple Brands | © Copyright 2025 Cube Purple LTD – All Rights Reserved – Powered by Cube Purple